What this threat is:
This latest threat actually has nothing to do with Adobe’s Flash product, but mimics as an updater for that product. You get attacked as you surf the Internet. Specifically,
- This is what is known as a “drive-by attack” – you just have to visit a malicious website, or an innocent website which has been compromised, and this attack will happen as you “drive by” with your web browser.
- As a Trojan Horse, it tricks you into thinking that it is a legitimate installer by mimicking the installer of a well-known software vendor.
Who is vulnerable:
This is a Windows based Trojan, so anyone running Windows from XP on upward should be cautious. The known web browsers to be affected (so far) by both the drive-by attack, as well as the subsequent changes to any browser settings, include Firefox, Chrome and Internet Explorer.
How it manifests:
It is impossible to know or be able to determine ahead of time which web sites to avoid. However, the Trojan is rather simple to identify.
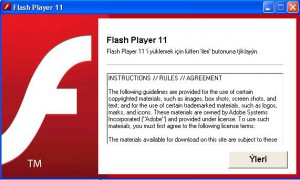
First, during the attempted attack, you will see this screen:
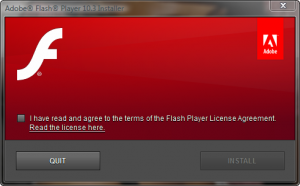
The key point to look out for are that some of its content is in Turkish. Always beware when an automatic updater presents content which is not in your computer’s standard language. Compare this to the official Adobe Flash Player Installer, as it has been since version 10:
This official installer looks far more refined, and has looked like this for many releases so far.
Secondly, if you actually become infected, your home page will change to one of the following addresses:
- www.anasayfada.net
- www.heydex.com
Basic actions needed:
If you do see the Trojan, cancel the operation. It will not install if it is cancelled.
If it has been installed, ensure your Antivirus software is updated and is functioning properly. Use a third-party online scanner to ensure that this malware has been fully removed. Remember, if you cannot reach a popular online scanner, there is most likely a piece of malware preventing you from doing so!
Additional actions needed:
If you use Internet Explorer, the icons you click on to launch it may have been “contaminated” with extra instructions that an Antivirus will not remove (because those instructions are not, by themselves, a danger). If you find you cannot launch Internet Explorer after cleaning your computer, or if it continues to bring up non-standard web sites instead of your home page, follow these instructions:
- Find any icon that you would normally use to launch IE.
- Right-click on the icon, choose Properties from the pop-up menu.
- In the Target field, delete everything after iexplore.exe, including any URLs.
- Click OK.
- Rinse-and-repeat for any other Internet Explorer icons:
- If you make use of Windows 7, an IE icon in the task bar can be reached here: %AppData%\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar
- Any IE icon in the Windows XP Start menu that is labelled as Internet is there via another method should not need fixing.
More Information:
For those so inclined, you can read about Microsoft’s details about this Trojan.